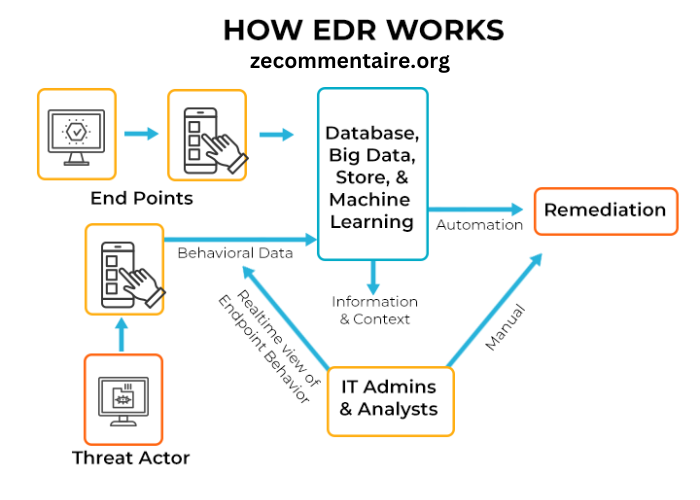
What Is EDR?
Understanding EDR (Endpoint Detection and Response) is crucial in cybersecurity. EDR refers to a system that monitors and responds to threats across various endpoints in a network. These endpoints can include servers, desktops, laptops, and mobile devices. The fast speed of digital transformation has caused these endpoints to become more at risk, making them the primary focus for cybercriminals. As such, EDR tools are pivotal in identifying, investigating, and mitigating suspicious activities, providing robust protection against cyber threats. Beyond detecting known threats, EDR solutions leverage advanced analytics, behavioral analysis, and machine learning to uncover anomalous activities that signify potential breaches.
Why Is EDR Important for Cybersecurity?
The complexity of cyber threats is constantly growing, rendering traditional antivirus solutions inadequate. A report from Forbes emphasizes how the necessity of EDR in modern cybersecurity cannot be overstated. Unlike traditional antivirus solutions that react to already known threats, EDR systems provide a proactive approach by continuously monitoring activities and detecting anomalies that may indicate hidden threats. This proactive stance is crucial for identifying and mitigating threats, including malware and ransomware, before they can cause significant damage. With cyberattacks becoming more sophisticated, EDR tools have become essential in ensuring a comprehensive security posture for any organization, providing peace of mind in an increasingly hostile digital world. Moreover, EDR solutions allow for better incident documentation and compliance reporting, vital for meeting regulatory requirements in various industries.
Key Benefits of EDR
Implementing EDR solutions provides a multitude of benefits that elevate an organization’s cybersecurity defenses:
- Enhanced Visibility: EDR tools offer comprehensive monitoring across endpoints, giving valuable insights into suspicious activities and potential threats. This enhanced visibility allows security teams to track and analyze events in real time, significantly improving their ability to protect critical assets. EDR solutions create detailed logs and dashboards that offer insights into endpoint behaviors, helping analysts quickly identify and respond to threats.
- Rapid Response: These tools enable quick responses to detected threats, significantly reducing potential cyberattack damage. By automating the detection and response processes, organizations can react to incidents in seconds rather than hours, thus minimizing the impact of breaches. Immediate threat containment features ensure that attacks are swiftly mitigated to prevent lateral movement across the network.
- Automated Analysis: Leveraging artificial intelligence and machine learning, EDR solutions can analyze and categorize threats automatically, making them efficient and highly effective. These advanced analytics help identify patterns, predict future attacks, and create robust threat intelligence that can be shared across the security ecosystem.
- Incident Investigation: EDR facilitates in-depth investigation into the root causes of security incidents, helping organizations understand and prevent similar future attacks. Detailed forensic analysis can provide insights into how an attack occurred, which vulnerabilities were exploited, and what steps must be taken to avoid recurrence, strengthening the overall security framework. This forensic capability is essential for post-incident reviews and improving future preparedness.
Real-Life Examples
Various sectors have seen significant benefits from implementing EDR solutions. For instance, the healthcare industry has been a prime example. A study published by Health IT Security illustrates how hospitals and healthcare providers use EDR to protect sensitive patient data from ransomware attacks. The healthcare sector, which deals with vast amounts of sensitive and personally identifiable information, has been a frequent target for cybercriminals. Implementations of EDR in these settings not only enhance their security posture but also enable them to respond swiftly to threats, thereby ensuring the integrity and confidentiality of patient data. This proactive strategy has been a game-changer in decreasing breaches and upholding trust in healthcare services. Furthermore, EDR solutions in healthcare have helped maintain compliance with standards such as HIPAA, thus avoiding hefty fines and reputational damage from data breaches.
Implementing EDR in Your Organization
For effective implementation of EDR in your organization, consider these steps:
- Assess the current security posture and identify gaps where EDR can be beneficial. Perform a comprehensive risk assessment to grasp the weaknesses and possible consequences of threats to your company. It involves evaluating the network architecture, identifying critical assets, and considering the specific threat landscape relevant to your industry.
- Choose an EDR solution that aligns with specific organizational needs and infrastructure. Evaluate different EDR tools based on their features, ease of integration, and scalability to ensure they meet your unique requirements. It’s important to consider whether the EDR solution can integrate seamlessly with other security tools and platforms in your environment.
- Train staff on the use and benefits of the EDR tools to ensure successful adoption. Practical training helps your team utilize the EDR solution to its fullest potential, improving security awareness and response times. Regular training sessions and simulation exercises can keep the security team prepared and proficient with the EDR system.
- Review and update EDR configurations regularly to adapt to evolving cyber threats. As cyber threats change frequently, defense mechanisms need to evolve constantly. Periodic reviews and updates will ensure that your EDR system remains effective against new and emerging threats. This also includes staying updated with the latest security patches and threat intelligence feeds provided by the EDR vendor.
Common Challenges and Solutions
While EDR offers substantial benefits, it also presents some challenges:
- Complexity: Implementing and managing EDR can be complex. Organizations should ensure their IT teams are well-equipped and trained to handle these tools effectively. Simplifying deployment through automated setup processes and user-friendly interfaces can mitigate this complexity. Additionally, seeking support from managed service providers (MSPs) can alleviate some of the complexities of EDR management.
- Cost: Smaller businesses may be concerned about EDR solutions. Exploring scalable solutions can help mitigate this issue, allowing smaller entities to benefit without straining their budgets. Many EDR providers offer tiered pricing models that can accommodate businesses of different sizes and needs. It’s also possible to start with a basic package and expand functionalities as the organization’s cybersecurity needs grow.
- Integration: Integrating EDR with existing security systems can pose challenges. Opt for comprehensive EDR platforms that support seamless integration with other security measures to enhance overall effectiveness. An integrated security ecosystem ensures that all components work harmoniously, providing a unified defense against threats. Organizations should seek EDR solutions that offer robust APIs and compatibility with their existing technology stack.
Future of EDR
The future of EDR looks promising with advancements in artificial intelligence and machine learning. These technologies will make EDR solutions more efficient in predicting and mitigating cyber threats. AI-driven analytics can provide deeper insights and more accurate threat predictions, enhancing the overall effectiveness of EDR systems. Additionally, integrating EDR with other security measures will create a more robust defense mechanism for organizations, safeguarding them against an ever-evolving threat landscape. As the cybersecurity landscape changes, the solutions to combat threats will also adapt, guaranteeing thorough security for everyone. Businesses and other organizations must stay ahead of these trends to protect their assets and maintain trust in an increasingly digital world. The focus will likely shift towards more predictive and autonomous security measures, where EDR systems could prevent attacks before they even materialize, marking a significant advancement in cybersecurity.